Governance Surveys
Directorship Magazine

Online Article
The Goldilocks Approach to SEC Cybersecurity Disclosures: Combine Regulatory Guidance With AI Analysis to Get it "Just Right"
Many publicly traded companies are struggling to understand how to get reporting obligations for public companies under the US Securities and Exchange Commission’s (SEC) new rules on cybersecurity risk management, strategy, governance, and incident disclosure “just right.” How much information is too little, and how much is too much?
The rules, which were adopted in July 2023 and went into effect Dec. 15, 2023, require both proactive and reactive cyber-risk disclosures. On an annual basis, registrants are required to proactively describe and disclose in Form 10-K specific information regarding their cybersecurity risk management, strategy, and governance. If a registrant experiences a material cybersecurity incident, they are required to reactively disclose the incident in Form 8-K within four business days of determining materiality. Shortly before these new rules went into effect, the SEC brought a civil complaint against a business and its chief information security officer, alleging negligence and failure to properly disclose risks and material incidents in both 10-K and 8-K forms. These new rules, coupled with the likelihood of enforcement actions, have left many companies and boards struggling with decisions about saying too little (not meeting the minimum SEC requirements) or saying too much (over-disclosing unnecessary information)—in other words, how to get it "just right."
Leveraging Artificial Intelligence (AI) to Analyze SEC Filing Trends
Proactive Disclosures: Analysis of 10-K Filings and Lessons Learned
Using our AI-powered benchmarking service that analyzes 10-K cyber-risk disclosures and provides insight on emerging trends, we learned that approximately 5,800 10-Ks (including 10-K/As) were filed between mid-December 2023 and April 2024. The top three sectors to file 10-K disclosures generally were health care, financial services, and industrials. Of the 10-Ks filed in this period, 80 percent offer fewer than 900 words for Item 1C. Cybersecurity Disclosures.
Reactive Disclosures: Analysis of 8-K Filings and Lessons Learned
A study of 8-Ks filed in the first six months since the new rules went into effect (i.e., Dec. 18, 2023, through June 18, 2024) provides critical guidance about disclosures and decision-making around materiality under the new rules. Using a large language model, our data science team analyzed 17 8-K forms (excluding 8-K/As) that report a cybersecurity incident under the mandatory reporting section of 8-K Item 1.05. The average word count of these 8-K filings was around 200 words, excluding forward-looking statements. Sixteen of the 17 8-Ks disclose the date the cybersecurity incident was detected. The timing of the filing ranged from 1 day to 43 days after detection of the incident, with an average of 8 days after detection. Eleven of these first 17 filings indicate that the financial impact had yet to be determined and only three mention material operational impact. In other words, companies are filing quickly—before financial impact has been determined—and keeping it brief.
Although the rule mandates reporting of material cybersecurity incidents, the overwhelming majority of companies that filed an 8-K in the first six months state they do not believe the incident was material or do not know if the incident would ultimately be material. Material cybersecurity incidents are defined in the Code of Federal Regulations as "an unauthorized occurrence, or a series of related unauthorized occurrences, on or conducted through a registrant's information systems that jeopardizes the confidentiality, integrity, or availability of a registrant's information system or any information residing therein." Without any clear precedent on what the SEC considers a "material cybersecurity incident" or what to include in Form 8-K, companies are erring on the side of caution by disclosing events that the company does not believe are material.
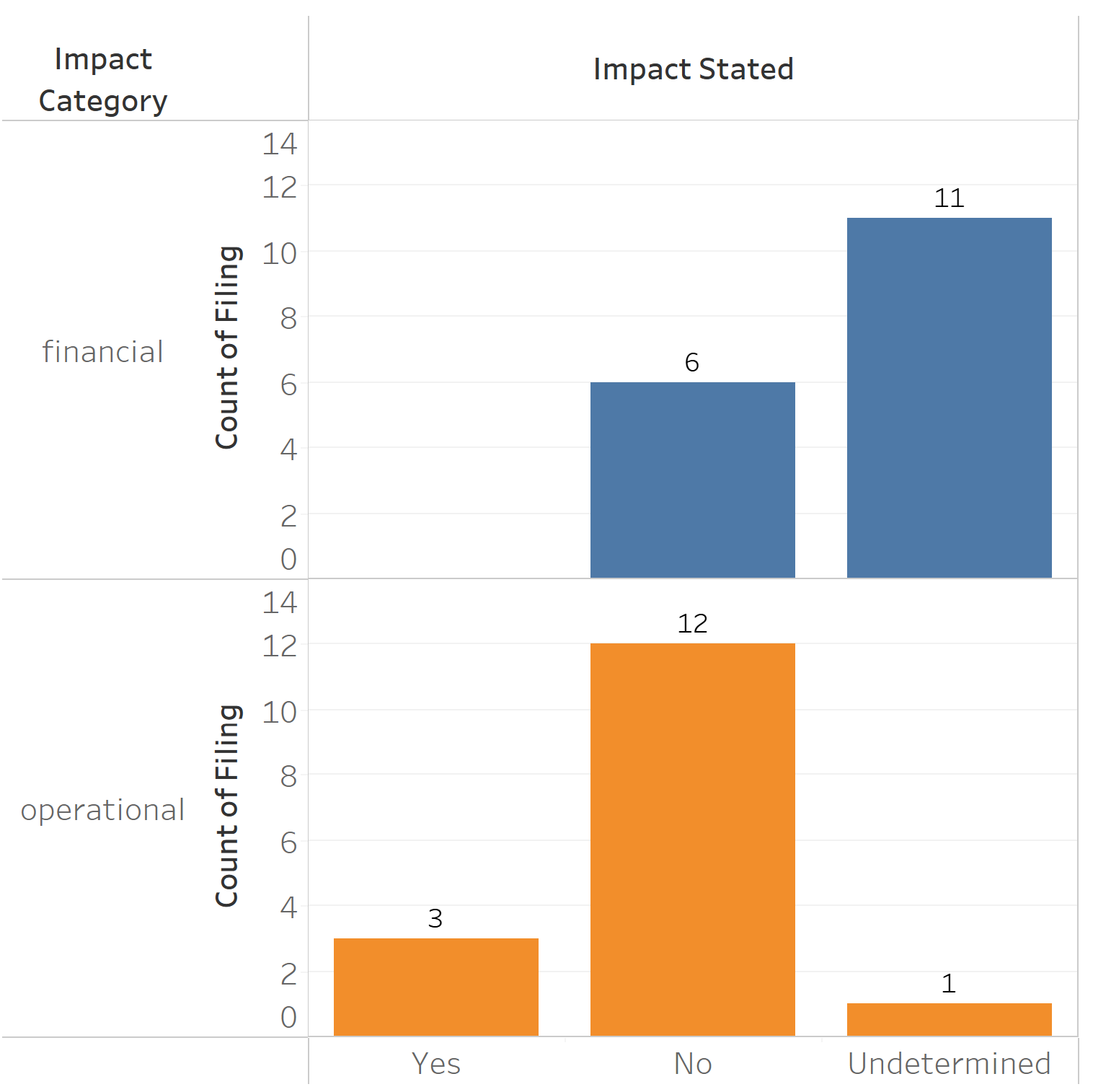
Source: Baker McKenzie, LLP 2024
In response to the recent trend of over-disclosing nonmaterial incidents in 8-K forms, the SEC issued “Disclosure of Cybersecurity Incidents Determined to Be Material and Other Cybersecurity Incidents” in May 2024, which explains that companies "choosing to disclose cybersecurity incidents for which [they] have not made a materiality determination, or a cybersecurity incident that was not material, should do so under a different item of Form 8-K (for example, Item 8.01)."
Developing a Defensible Process to Make Materiality Decisions
Determining materiality can be a difficult analysis that requires input from multiple stakeholders and continues to evolve throughout the incident lifecycle. In its May guidance, the SEC reminded companies to assess "all relevant factors" and not to limit their analysis solely to the impact on "financial condition and results of operation." Other "relevant factors" may include whether the incident will harm its reputation, customer or vendor relationships, competitiveness, and the possibility of litigation or regulatory investigations or actions. The new SEC rules mandate the business develop a "process for assessing, identifying, and managing material risks from cybersecurity threats." Developing a playbook or checklist that elicits questions about "all relevant factors" specific to the organization can provide a helpful road map during crisis management and also demonstrate compliance with the SEC cybersecurity governance requirements.
Preparing Disclosure Language: Too Much or Too Little?
After determining a cyber incident is material, the business must then decide how much or little to disclose in the 8-K filing. Is it sufficient to state that a material incident occurred and an investigation is ongoing, or should a company provide details about the timeline, the investigation, and the financial and operational impact? Though the SEC has not provided concrete guidance, a recent US Supreme Court case suggests saying less may be less risky. In a recent watershed ruling, the High Court held that pure omissions from an SEC filing may not support a claim for securities fraud under Rule 10b-5(b). Though the decision involved environmental disclosures, the same argument can be made for cybersecurity disclosures in Item 1.05; there can be no 10b-5(b) liability for "pure omissions." The ruling may curtail civil liability for securities fraud, making it more challenging for plaintiffs to state a claim under Rule 10b-5(b) for failure to disclose. But the High Court also highlighted that the SEC could still pursue enforcement actions for both pure omissions and half-truths. Though companies are still required to file within four business days of a material cybersecurity incident, this recent precedent suggests that it may be less risky to say "too little" when filing the initial 8-K.
Extensions, Materiality, and Selective Omissions When Filing an 8-K
If a business believes an incident could be material, they must also consider whether public disclosure of the incident may pose a risk to national security or public safety. Will the filing disclose a previously unknown supply chain vulnerability, thereby creating a risk to other businesses or critical infrastructure? Does the breached system contain sensitive data that could create a risk to national security? If so, the US Department of Justice (DOJ) may grant an extension to delay filing a public notice via Form 8-K as described in its “Cybersecurity Incident Delay Determinations.” Notably, the DOJ stresses that this analysis should occur first—even before a materiality decision is made—and the Federal Bureau of Investigation should be contacted immediately if a company believes an exemption may apply. While this exemption is unlikely to apply to most cybersecurity incidents, it may grant companies more time to investigate and contain an incident before going public.
How to Get it "Just Right" and Where This Leaves Companies
With guidance coming from all angles, the golden question remains: How do companies get their 8-K and 10-K cybersecurity disclosures "just right?” The US Supreme Court ruling suggests there is a legitimate basis for omitting certain disclosures, and the SEC guidance encourages waiting until a materiality decision is made before filing a mandatory disclosure. Businesses do not want to be at the front of the pack by disclosing too much, nor do they want to be at the back of the pack by disclosing too little. Boards can use the actionable guidance below to help companies get their proactive and reactive SEC cybersecurity disclosures "just right:"
- Receive regular briefings on cyber risk management. Inquire specifically about how the business is assessing, identifying, and managing material cyber risks. Regular briefings can build rapport and trust with leaders managing cyber risk and require the business to prioritize and articulate key risks. These briefings allow the board to exercise meaningful oversight of the people, processes, and technologies that are keeping the business secure.
- Refresh incident response policies and develop a materiality playbook. Develop a framework or playbook for determining whether a cybersecurity incident is material and reportable to ensure that the business complies with relevant deadlines. Include a checklist of key questions whose answers will inform whether an incident may be considered material. Additionally, include a section to consider whether public disclosure of the incident may give rise to issues of national security or public health and safety.
- Test SEC materiality decision-making with tabletop exercises. Pressure test the materiality playbook through tabletop exercises using real-life scenarios to determine whether various types of incidents may or may not be material, then refine it to account for additional questions or issues that may need to be included for decision-making. Conducting these tabletop exercises allows the business to develop a risk appetite and define roles and responsibilities related to determining and overseeing materiality in the lifecycle of a cyberattack. Reporting the results of the materiality tabletop exercises gives directors an opportunity to ensure the risk appetite of management and the board are aligned.
- Cyber risk is everyone's responsibility. Ensure the business has a cross-disciplinary team of leaders from information security and technology, legal, risk management, audit, communications, investor relations, human resources, and finance groups to build the cyber-risk governance program. This team can be responsible for developing and implementing various aspects of the cyber-risk governance program, including materiality decision-making, processes to manage and respond to cybersecurity risks in compliance with the SEC rules, and training for incident response teams to understand reporting obligations.
- Develop processes and holding statements. Develop processes that require both technical and legal input for the development of regulatory filings and create proactive and reactive cybersecurity language that is vetted and can be used in filings when needed.
- Benchmark against peers. Conduct an analysis to measure 10-K cyber disclosures against peers to ensure that the company’s disclosures are aligned with industry standards.
- Stay up to date. Stay on top of this evolving area of law as the SEC continues to issue guidance and businesses interpret the new rules.
This analysis and article were prepared by Baker McKenzie's cybersecurity team in collaboration with BakerML, a multidisciplinary practice team (data scientists, lawyers, engineers, and other technical and domain experts) that combines Baker McKenzie’s legal expertise and knowhow with data science, machine learning, and other advanced AI to better serve our clients.

Justine Phillips is a partner at Baker McKenzie.

Zonghui Wei is a senior data scientist with Baker McKenzie's Machine Learning practice (BakerML).

Ella Noll is an associate at Baker McKenzie.

