
Governance Surveys

What Directors Can Learn From Cyber Incident Disclosures
A Zscaler analysis of US Securities and Exchange Commission (SEC) filings on cyber incidents gives a snapshot into the effect of cyberattacks—especially ransomware—on public companies and how disclosures are affecting the stock price of victim companies.
Following adoption of the SEC’s Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure rule on July 26, 2023, public companies are now required to report incidents along with an assessment of their materiality within four business days via an 8-K form.
In the 12 months ending on July 26, 2024, 42 companies reported cyber incidents, including nine that followed the new rule voluntarily before it officially started on December 18, 2023.
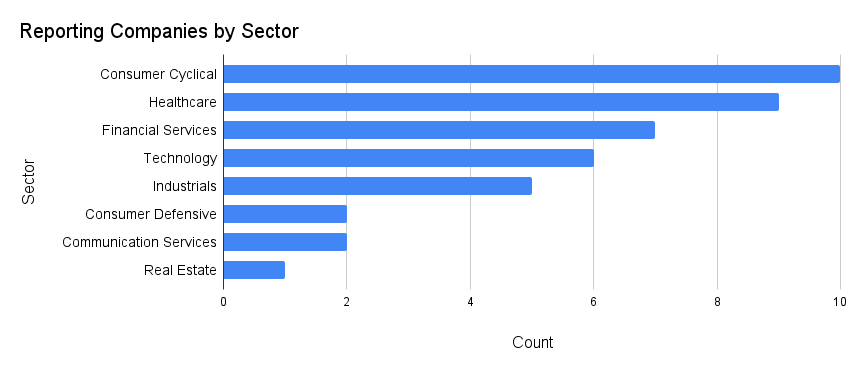
Consumer Cyclical and Health-care Companies Most Frequently Targeted
Consumer cyclical companies, including an apparel manufacturer and several auto and truck dealerships, disclosed 10 incidents, followed closely by health-care companies, such as Henry Schein and Cencora, with nine disclosed incidents. Financial services and technology organizations also regularly reported incidents.
Ransomware infections drove most of the filings, and one attack that stood out in particular was UnitedHealth Group’s Change Healthcare business unit in February 2024. In the company’s second quarter earnings report, four months after the attack, total costs stood at $1,982 million, including a $22 million ransom paid to hackers. That total is projected to rise to between $2.3 billion and $2.45 billion in 2024.
Protecting businesses from ransomware attacks should be a director’s top cyber priority. Hackers are currently exploiting outdated technologies, such as virtual private networks and firewalls to compromise networks, yet many companies have not adopted a zero trust architecture, which would stop the attacker’s ability to spread malware throughout the network.
The Effect of a Disclosure on Stock Price
Currently, at least one month of post-incident stock-price data are available for 34 of the reporting companies. Stock at over half (56%) of the aforementioned companies remained below the pre-incident price after one month, with an average decrease of 8.8 percent.
Directors should be aware that disclosures tend not to lead to sudden drops in stock price; UnitedHealth’s stock rose by almost 1 percent on the day of its announcement. However, prices will be impacted by factors in the days and weeks that follow, including the perceived cyber expertise of management and the board and their handling of the incident.
It is extremely difficult to determine the full extent of the damage from a cyber attack within the reporting window. Waiting until the end of the four-day period before disclosing means the materiality assessment is more likely to be accurate, which reduces the risk of having to issue corrections.
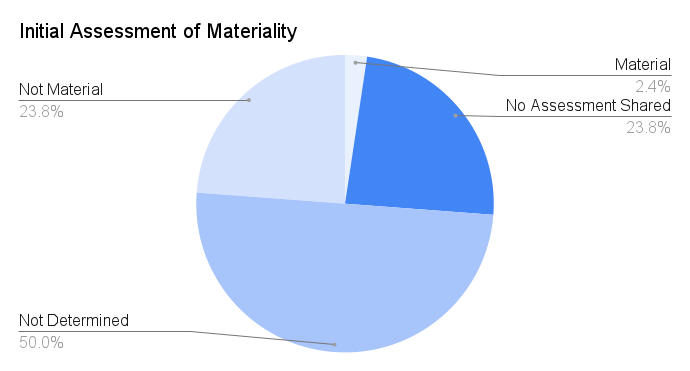
Materiality Assessment
Of the 42 disclosures made, only one included an assessment that the incident would be material to the business, though the company subsequently reported that was not the case. Exactly half of disclosures said the assessment of materiality had not been determined, and just under one quarter said there had been no material impact. Seven of the 10 companies that did not share any assessment of materiality made their disclosures before the requirement came into effect.
The disruption to operations and customers is the focus of media reporting immediately after an incident. This does not only stem from attackers; directors should be aware that it can occur as the result of the victim’s efforts to contain the attack. Addressing the source of the disruption in the filing helps investors understand the extent to which it is controlled.
Third-Party Cyber Victims
Filings from five auto and truck dealerships and a software company are a reminder to directors of the criticality of third-party cyber risk management. The auto industry companies filed reports in June 2024 related to an incident at their common supplier, CDK Global, a maker of auto dealership software. Disruption at CDK Global meant an outage of software used to process car sales.
Industries that rely on a small pool of suppliers are at risk of a major setback if one of them fails. Directors should check that management has identified critical third-party suppliers and has a plan for business continuity in the face of outages lasting from several hours to several weeks.
A Focus on Robust Oversight
Directors must also take immediate action in fortifying their defenses to avoid falling prey to cybercriminals who are increasingly using artificial intelligence (AI) to enhance their capabilities. This comes at a time when many companies are taking a more cautious approach to AI.
Despite the countless publicized cyberattacks over the last decade and clear guidance on securing networks from authorities such as the National Institute of Standards and Technology (NIST), directors cannot assume the businesses they oversee are either fully prepared to counter attacks or are resilient enough to quickly restore normal operations after an incident. The role of directors in cybersecurity is not just a matter of compliance, but a critical component of strategic leadership and corporate governance. By adopting a proactive stance and integrating advanced security frameworks like zero trust, which NIST recommends, directors can significantly mitigate risks, protect against data loss and ransomware, and avoid the potentially devastating consequences of cyberattacks.
Zscaler is a NACD partner, providing directors with critical and timely information, and perspectives. Zscaler is a financial supporter of the NACD.

Rob Sloan is the vice president of cybersecurity advocacy at Zscaler.